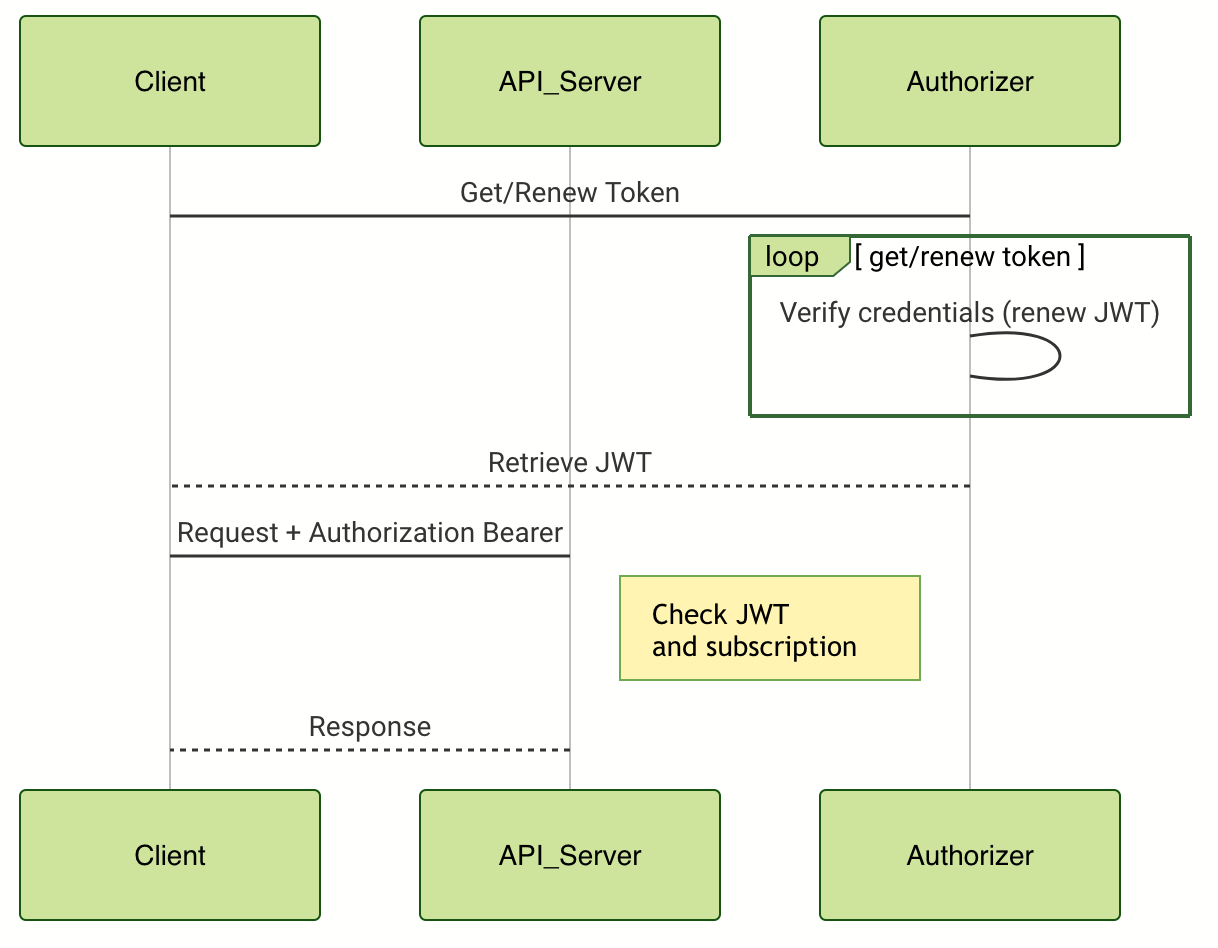
# The e-Attestations REST API uses [OpenID Connect (OIDC)] (https://openid.net/connect/ ) to identify and authenticate clients.
Any request to the API is verified thus must include a valid JWT (Json Web Token ).
This must be sent in the Authorization header (see examples below).
If the Authorization header is not completed and valid, the request will be considered as not authenticated (HTTP code 401).
If any alteration of the token happens (IP address change is one of them) you'll receive HTTP code 403.
More information on OpenID Connect and JWT on:
# The security model use a standard Header Authorization: Bearer <JWT>model.
But you need credenials in order to obtain a JWT.
Your credentials have to be issued at your request via a techDesk ticket and after activation of your subscription by your account manager.
Please send an email to api@eattestationscom.zohodesk.eu
# To get a JWT token you need to do a POST type request with user and password and some additional parameters to the authentication server.
Parameter Mandatory Value Description client_id true 'ea-api-edge' The name of the API grant_type true 'password' The authentication model username true The username given by e-Attestations password true The password given by e-Attestations
You must send a request in application/x-www-form-urlencoded Content-Type header format with the following parameters (all mandatory):
Obtain a JWT
Copy curl --request POST 'https://auth.test-e-attestations.com/auth/realms/eat_realm/protocol/openid-connect/token' \
--data-urlencode 'grant_type=password' \
--data-urlencode 'client_id=ea-api-edge' \
--data-urlencode 'username=<your user>' \
--data-urlencode 'password=<your password>' \
--data-urlencode 'Content-Type=application/json'
The authentication server will return a JSON word in which it is necessary to preserve the 'access_token'.
Credentials are verified by the auth server which send back a JWT (JSON Web Token) that user have to keep in ordre to use it for all subsequent requests to the API.
Example of the receive message
Copy {
"access_token" : "eyJhbGciOiJSUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICI0V19kYjFzUmpISTc3SGc0SkRWclVLQXpaQlBnZjlpY2ZDcU5vQUxOZWhNIn0.eyJqdGkiOiI0ZGExNjE1NC04ZjQyLTQyNzQtOTM4Ny0wOGJiODk4MmE3MTMiLCJleHAiOjE1NTQyOTgyNTgsIm5iZiI6MCwiaWF0IjoxNTU0Mjk2NDU4LCJpc3MiOiJodHRwczovL2F1dGguZGV2LWUtYXR0ZXN0YXRpb25zLmNvbS9hdXRoL3JlYWxtcy9lYXRfcmVhbG0iLCJhdWQiOiJhY2NvdW50Iiwic3ViIjoiYzg0OGFiYmItYTIyOC00MmMxLWFkNzAtYjJiMDEwYzhlODUxIiwidHlwIjoiQmVhcmVyIiwiYXpwIjoiZWEtYXBpLWVkZ2UiLCJhdXRoX3RpbWUiOjAsInNlc3Npb25fc3RhdGUiOiI5YmEzYWFmNC0zYjU0LTQ5ZTctOTJiMC0xOTkwMGQxNWE5ZWIiLCJhY3IiOqsdqsdsdqsdqsdsaW5lX2FjY2VzcyIsInVtYV9hdXRob3JpemF0aW9uIiwiQURNSU4iLCJVU0VSIl19LCJyZXNvdXJjZV9hY2Nlc3MiOnsiYWNjb3VudCI6eyJyb2xlcyI6WyJtYW5hZ2UtYWNjb3VudCIsIm1hbmFnZS1hY2NvdW50LWxpbmtzIiwidmlldy1wcm9maWxlIl19fSwic2NvcGUiOiJwcm9maWxlIGVtYWlsIiwiYWNjb3VudF9pZHMiOiIxMTg0NjYiLCJlbWFpbF92ZXJpZmllZCI6dHJ1ZSwibmFtZSI6IlZpbmNlbnQgREFHT1VSWSIsInByZWZlcnJlZF91c2VybmFtZSI6InYuZGFnb3VyeUBlLWF0dGVzdGF0aW9ucy5jb20iLCJnaXZlbl9uYW1lIjoiVmluY2VudCIsImZhbWlseV9uYW1lIjoiREFHT1VSWSIsImVtYWlsIjoidi5kYWdvdXJ5QGUtYXR0ZXN0YXRpb25zLmNvbSJ9.c-smWPif1YT9dKicAAJSsNwI-xCtZWV-r6QqYFSvkgHhPsgHc0gDLenMfQBgYPN_0jKW7FBJmse7fgAB4dnrqCOGM33cQ2wfYi37aXlDqz8l_aFamkEslGnKxw9QDOYSMQz52dD34yXQZGl0OxXE01PAquqKUEtnVG0Rz2SAB0qU5tAqsdqsdsd-rKpCYwKb_6-WwH2xN1B9lgLahZexprPvH25OXUcPJ0GSXCASpnSMxR3ziiv9AtX3R48rT4T_LTLlrKblT_cdZS-Z_uGgzP0pxT9yfqxSYn05haRLTL_grBDdt31ZIDnxiMFEg2UdDB1wzlJBOuOEmw" ,
"expires_in" : 1800 ,
"refresh_expires_in" : 1800 ,
"refresh_token" : "eyJhbGciOiJIUzI1NiIsInR5cCIgOiAiSldUIiwia2lkIiA6ICJiYTcxZWMyOC0wOTVkLTRkOWQtOWQwYi1jYjAyMTJmNjczYjcifQ.eyJqdGkiOiI2YmQ2ZThkYS1kOWNjLTRhNzgtODg1NS1iMzMwZWU0NDg1NjEiLCJleHAiOjE1NTQyOTgyNTgsIm5iZiI6MCwiaWF0IjoxNTU0Mjk2NDUqsdqsdqsdqsdOiJodHRwczovL2F1dGguZGV2LWUtYXR0ZXN0YXRpb25zLmNvbS9hdXRoL3JlYWxtcy9lYXRfcmVhbG0iLCJhdWQiOiJodHRwczovL2F1dGguZGV2LWUtYXR0ZXN0YXRpb25zLmNvbS9hdXRoL3JlYWxtcy9lYXRfcmVhbG0iLCJzdWIiOiJjODQ4YWJiYi1hMjI4LTQyYzEtYWQ3MC1iMmIwMTBjOGU4NTEiLCJ0eXAiOiJSZWZyZXNoIiwiYXpwIjoiZWEtYXBpLWVkZ2UiLCJhdXRoX3RpbWUiOjAsInNlc3Npb25fc3RhdGUiOiI5YmqsdqsdsqsdQ5ZTctOTJiMC0xOTkwMGQxNWE5ZWIiLCJyZWFsbV9hY2Nlc3MiOnsicm9sZXMiOlsib2ZmbGluZV9hY2Nlc3MiLCJ1bWFfYXV0aG9yaXphdGlvbiIsIkFETUlOIiwiVVNFUiJdfSwicmVzb3VyY2VfYWNjZXNzIjp7ImFjY291bnQiOnsicm9sZXMiOlsibWFuYWdlLWFjY291bnQiLCJtYW5hZ2UtYWNjb3VudC1saW5rcyIsInZpZXctcHJvZmlsZSJdfX0sInNjb3BlIjoicHJvZmlsZSBlbWFpbCJ9.fpVVA-G-Fj9MDOB5ZneAGVRhkLk26hgCeZ4dqh3rEHs" ,
"token_type" : "bearer" ,
"not-before-policy" : 1550670103 ,
"session_state" : "9ba3aaf4-3b54-49e7-92b0-19900d15a9eb" ,
"scope" : "profile email"
}
The token has a limited life time which can be verified with expires_in expressed in seconds and fixed to 1800s (30 minutes).
Each request are authenticated with this access_token placed in a Authorization: bearer <your access_token> header for each request.
# We provide you with a auth server per environment like so :
The authorization server for production is https://auth.e-attestations.com The authorization server for testing is https://auth.test-e-attestations.com # You can also ask for an renewed access_token by using the refresh tokenso that you don't have to send again your credentials.
Note that it depends on expiration (refresh_expires_in) of the parent request expiration.
Copy Method: POST
URL: https://auth.test-e-attestations.com/auth/realms/eat_realm/protocol/openid-connect/token
Body type: x-www-form-urlencoded
Form fields:
client_id : ea-api-edge
grant_type : refresh_token
refresh_token: <your-refresh-token>
# is valid for a limited time. You must make sure of the duration of validity of your TOKEN thanks to the data "expires_in" which indicates the number of seconds before it expires (for example 1800 seconds corresponding to 30 ') is to be used in all API requests resides in the access_token property needs to be set within an Authorization HTTP Header Example
Copy curl -X GET \
https://api.test-e-attestations.com/api/v1/account/97862/dossiers \
-H "Authorization: Bearer <JWT_TOKEN>"